I am frequently asked about how VeriClouds Identity Threat Protection is any different than the free service Have I Been Pwned (HIBP). As the world’s obsession with whether they have been pwned or not became more obsessive and more compulsive, my team at VeriClouds was busy building the next generation credential monitoring and verification platform. Free is not always free, and organizations using HIBP’s password dumps and APIs put their users at higher risk compared to using an identity threat protection service, such as
CredVerify. ‘;–
Don’t get me wrong, my team has a lot of respect for Troy. What he built with HIBP has helped raise awareness on a global stage about the devastating effects that data breaches have to businesses and end users. Troy built a massive following of journalists and fans who love to cite his work almost exclusively. In effect, with HIBP, everyone now knows that we have in fact been pwnd.
The HIBP service is great for detection of data breaches, but it offers nothing to help with verification (of compromised credentials) and on-going protection for businesses and users. That is the space where VeriClouds focused its R&D and product development cycles for the past three years, and one that cybersecurity leaders should be paying much closer attention to in the post-breach world we now live in.
VeriClouds Leads with Privacy by Design
Since the inception of our product, everything we’ve ever done for handling sensitive credential data begins with privacy by design and by default. From the use of data masking and encryption to achieving privacy protection (e.g., k-anonymity) while using our CredVerify and Password APIs, our database always protects the privacy on behalf of the rightful owners of the data.
Contrast VeriClouds’ approach to when HIBP first dumped a list of 320 million hashed passwords in September of 2017. It was
caught by researchers who noticed that the dump contained personally identifiable information when the credentials were reversed, even linking the hash to the owner of the password!
In August 2017, VeriClouds’ CTO Rui Wang, a former Microsoft security researcher with his Ph.D. in Cybersecurity
observed that HIBP reveals sensitive data such as breach source that may be used by an attacker to profile users for targeted attacks.
In today’s heavily regulated business landscape, such a leak could result in damages to brand reputation, fines under GDPR, HIPAA and the forthcoming California Consumer Privacy Act of 2018. In this example, it was reckless of HIBP to dump such data without considering the consequences to the privacy of the users who might have been affected.
A Better Balance Between Security and UX
These days there is a lot of pressure on product managers and solution architects to deliver end-to-end protection with as little impact to user experience as possible. Users have long been annoyed by entering in one-time passcodes for account security and using a blacklist of passwords is not especially new or novel.
In the same research previously referenced, experts weighed in that “…even if blocking common passwords during account creation has positive effects on the overall password security of a website, blacklisting the entire Hunt’s archive can have unforeseeable consequences on usability.”
According to research on HIBP’s password dump performed in VeriClouds’ lab, it was observed that without the identity context (e.g. using only the password list from HIBP) one would warn end-users to hypothetical risk of compromised credentials 2-6 times more than necessary, compared to using CredVerify which preserves the identity context of credentials and detects real and verifiable risk.
We believe that investing in identity threat protection is to invest in improving user experiences while simultaneously delivering safer online experiences for users.
Breach Detection ≠ Identity Threat Protection
It is no longer enough to answer the question, “Has my email been compromised or found in a data breach?” Leading security practitioners assume a state of breach. Forward-thinking organizations have begun adopting advanced cloud security services that help answer the question, “How at risk are my users and is my organization to the risk of compromised credentials?”
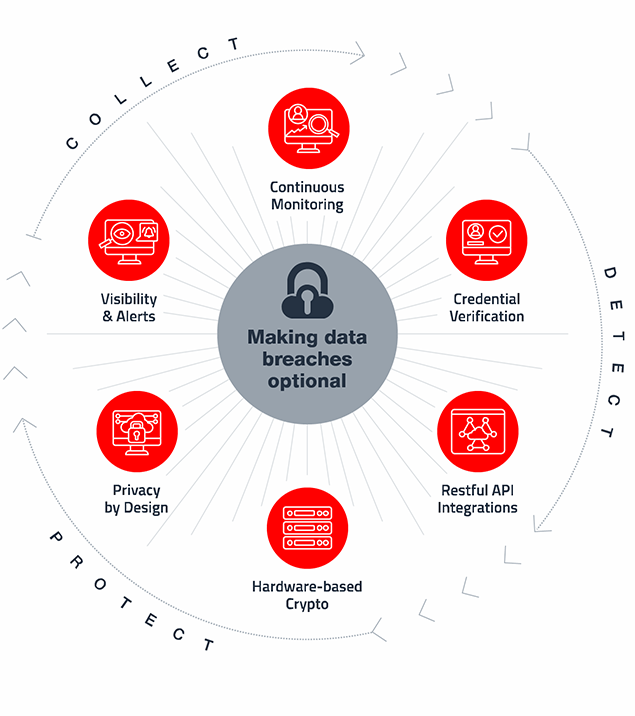
With VeriClouds’ Identity Threat Protection, shown in Figure 1, organizations can have a cloud-scale single pane of glass view of the compromised credentials threat landscape that far exceeds what cyber-criminals and bad actors have available to them.
Figure 1: VeriClouds Identity Threat Protection
Security and risk management leaders must be engaged with more than breach notification and password blacklists. Your system for monitoring and verification of compromised credentials needs to be able to answer:
- Are my current passwords leaked or reused?
- How at risk are the executives and privileged users in my organization?
- How do I only notify affected users without forcing a global password reset?
- How can I verify compromised credentials without ever revealing the account identifier or the credential to the service provider?
- Does this user’s leaked credential satisfy or violate my organization’s password policy?
There are more nuances to the detection and treatment of user-centric risk than knowing if the email address alone was involved in a data breach or if the password is considered weak, as HIBP offers to tell you. In other words, your email address may appear in the HIBP database, and not be pwned at all. Conversely, your email address may not appear in HIBP and still be at high risk.
Credential Analytics Delivers Actionable Intelligence
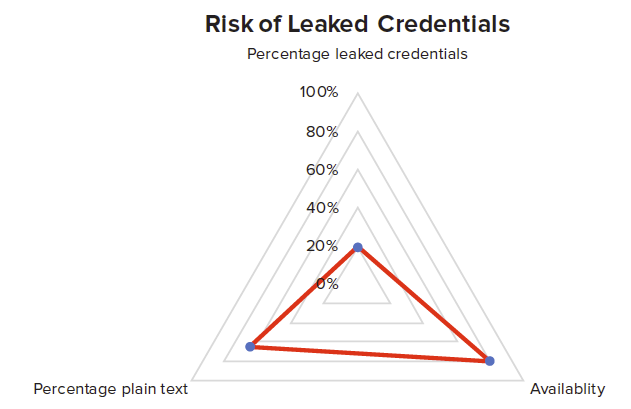
On the dark and surface webs, one will find vast troves of credential data readily available to nation-state actors and cybercriminals. As demonstrated in Figure 2, the risk that compromised credentials pose to users and business increases exponentially the longer they lay exposed online.
Figure 2: How at risk are your users and organization to compromised credentials?
VeriClouds has been collecting publicly available breached credentials since 2014, including from the English and Chinese speaking black markets. VeriClouds built its proprietary semi-automatic crawling engine to continuously collect breached databases from the dark web. Moreover, VeriClouds data analysts monitor all the various dark web forums and marketplaces daily to obtain newly breached credential databases when they become available.
VeriClouds used sampling to estimate the coverage that VeriClouds has about databases circulating on the dark web. Specifically, VeriClouds randomly sampled 100 databases found on the dark web and checked them against VeriClouds collections. VeriClouds found that 93 of the databases were already included in our collections. This test allows VeriClouds to claim over 90% coverage with high confidence.
The HIBP database understandably contains much less data, because it only needs one unique record per incident which is then used to notify users of an account breach, but does not provide whether the actual credentials being used are still at risk.
When it comes to data collection and management for identity threat intelligence, applying 80/20 thinking will endanger an organization. 20% of the leaked data does not mitigate 80% of the risk. Better data = better customer experience = better company performance.
At VeriClouds, we recover sensitive breach data from all the various sources to provide visibility and protection on behalf of the rightful owners of that data. Whether it comes from the ‘dark web’ or ‘surface web’ or anywhere else for that matter isn’t worth my breath arguing about it.
Enterprise Ready Identity Threat Protection
Thinking about the VeriClouds Identity Threat Protection platform in terms of customer value led my team to prioritize integrating with leading global identity and access management platforms via our value-added solution accelerators that optimize the value that may be captured by the customer. VeriClouds’ value hypothesis has always been focused on reducing the risk of collecting and handling sensitive breach data and automating the transformation of user-centric risk into response and remediation.
With VeriClouds-powered credential verification, more than 9 billion compromised credentials are surfaced to enable the automation of risk insight into actionable identity threat intelligence for Lieberman Software,
ForgeRock OpenAM and OpenIDM, Active Directory and SailPoint IIQ customers. This integration is code complete, tested and available today, dramatically improving the security and compliance posture for VeriClouds customers.
Organizations can experience the power of big data and credential analytics, a next-gen identity threat protection solution that provides visibility into the risk of user and machine identities. The breadth and depth of coverage provided by VeriClouds’ Identity Threat Protection is superior to what cybercriminals and nation-state actors have available to them. Data breach avoidance is a far better ethical use of compromised credentials (including keys and tokens) and enables safer online experiences. Peace of mind can be achieved knowing that better data and greater visibility can be automated for improved business performance.
Summary of key points
* VeriClouds delivers the safest and most secure way to verify compromised credentials
* VeriClouds begins and ends product development with privacy by design and default
* VeriClouds offers coverage of over 90% of all the leaked credentials on the dark web
* VeriClouds platform is designed for rapid ROI and time-to-value
* FOR PARTNERS: VeriClouds offers a robust platform with a superior monetization model for OEM/white label resellers
Also by Steve Tout: