Passwords Are The Weakest Link In Cybersecurity
Stolen or weak passwords are the most common reason for cybersecurity breaches.
When it comes to stolen or weak credentials of employees or customers, very few organizations can distinguish the genuine user from the sophisticated hacker during an attack.
Even if you enforce password policies and multi-factor authentication, considerable risk remains.
You need a solution that allows you to quickly identify when credentials have been compromised or used - and to act on that insight in real-time.

VeriClouds Services
VeriClouds has built - and continues to add to - a proprietary database of more than seven billion known credentials leaked on the dark web.
We use this repository to detect, verify, and remediate user-centric risks across a broad range of end-points, online services, and infrastructure.
- CredVerify - An API that detects compromised credentials by comparing your employees' or customers' credentials against VeriClouds’ database.
- CredMonitor - This service continuously monitors your domain on the dark web for leaked credentials.
- On-premise service - Query the VeriClouds database through a hardware appliance that runs within your internal network without requiring any connectivity to the outside.
- Integrations - Our services include agents that enable protection schemes for popular services such as Exchange/Active Directory, Oracle, Sailpoint, Lieberman Software, and Rest API for custom integration.
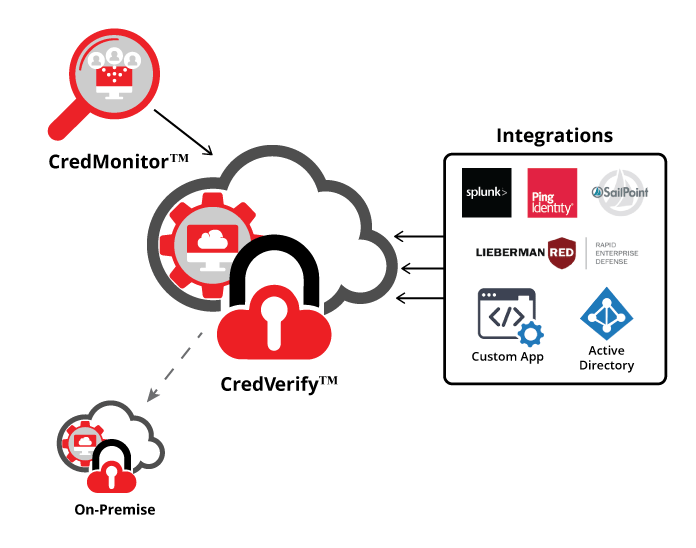

CredVerify
CredVerify API integrates with IAM systems to detect and verify compromised credentials

CredMonitor
CredMonitor web portal displays the leaked credentials of your organization
15% to 40% of a typical company’s credentials already exist in the VeriClouds database
Benefits of VeriClouds Services
![]()
- Scalable Our cloud and on-premise services can grow with you
- Secure Built from the ground up with privacy and security in mind
- Comprehensive The industry’s largest repository of known compromised credentials
- Easy to deploy Integrations with popular IDaaS providers and IAM systems
VeriClouds CredVerify enables organizations with risk-informed IAM by providing visibility into more than 90% of the leaked databases on the dark web.
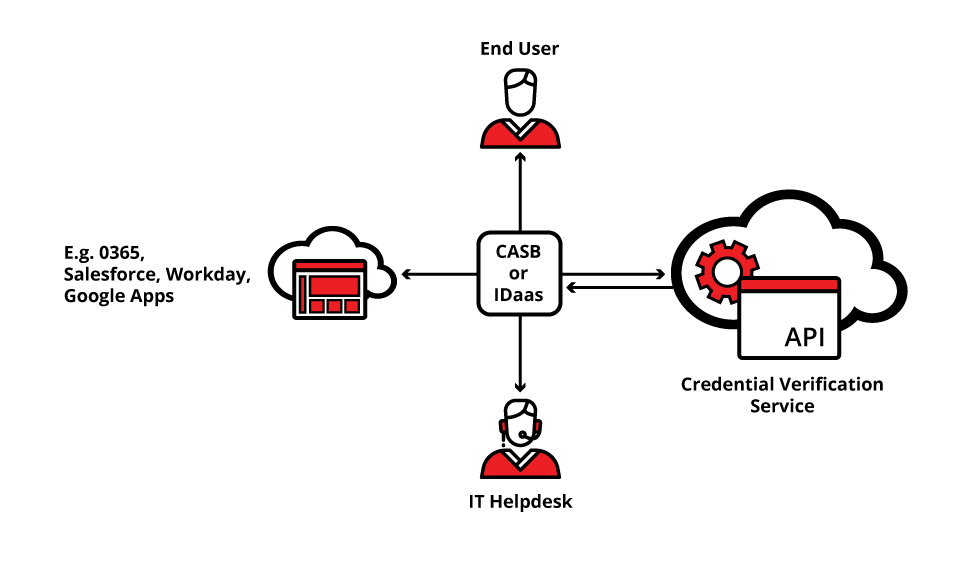
VeriClouds for CASB & IDaaS Providers
VeriClouds automates the mitigation of known compromised accounts to reduce the risk and costs that occur as a result of compromised credentials attacks, phishing, and wide-spread data breaches.
With our Rest API, the value of VeriClouds can scale to millions of users accessing IP and sensitive data on SaaS services and IaaS platforms.
An IDaaS that has knowledge of recently compromised accounts can detect the usage of a leaked credential and orchestrate full remediation, from notifying the end-user and forcing step-up authentication, to logging a ticket in a company’s help desk system.

Want to find out the two emerging compromised credential trends that could affect your exposure to risk? Contact us today.
Three ways to get in touch with us
- Call us at (844) 532 5332
- Send us an email at info@vericlouds.com
- Send us a message on Twitter @vericlouds

