Interop with CredVerify Shared Signals Framework
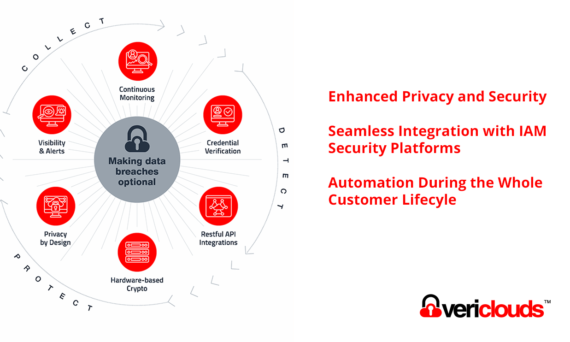
Interop with CredVerify Shared Signals Framework Transmitter for Compromised Credential Signal In collaboration with VeriClouds, Okta, SailPoint, Cisco, and Helisoft will demonstrate the interoperability of Shared Signal Framework’s Continuous Access Evaluation Protocol (CAEP) at the Gartner IAM Summit in London. For IAM developers, the critical question is how to obtain meaningful security signals efficiently. The […]