Assessing The Risk of Compromised Credentials to The Enterprise
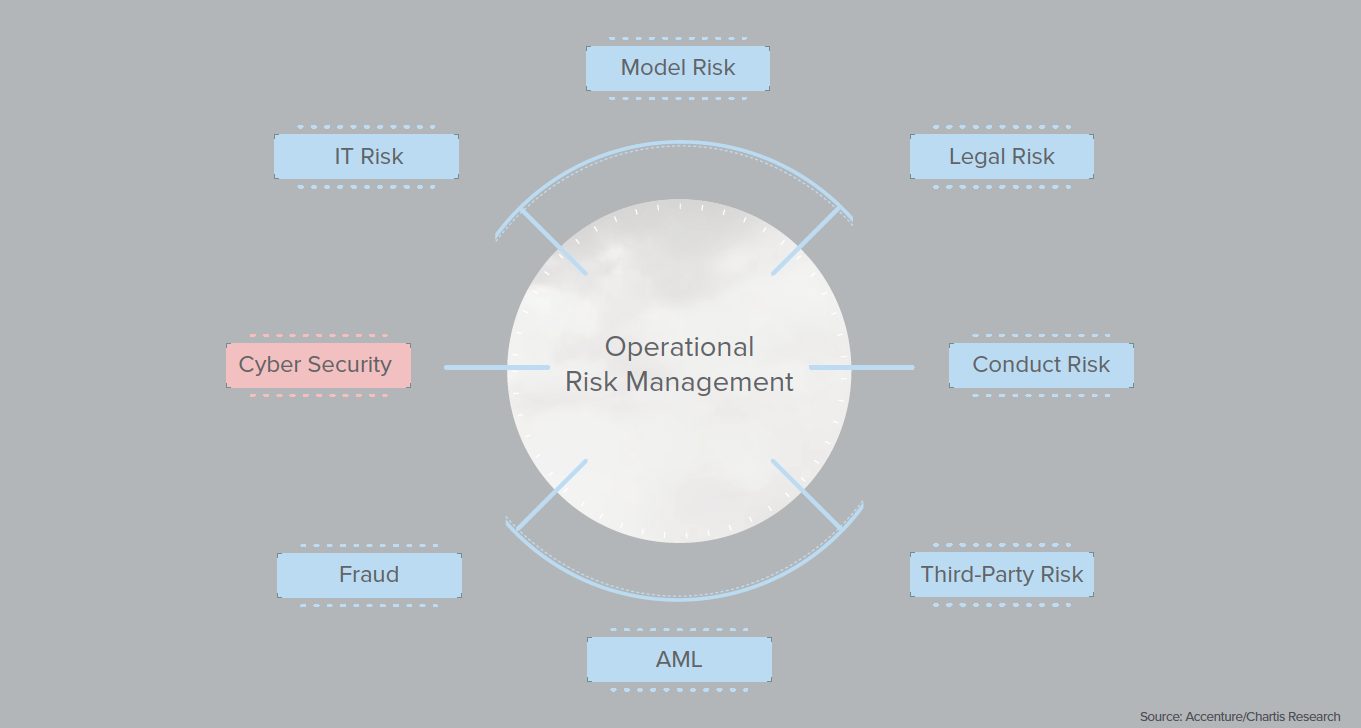
Businesses today face an abundance of organizational risk. These come in the form of creating the business model itself, dealing with third parties, managing vendors and partners, monitoring internal and external fiscal fraud, exercising premise security, and the like. In the 21st century, no greater risk is posed to the enterprise than that of risk to the technology infrastructure in the form of cybersecurity risk.
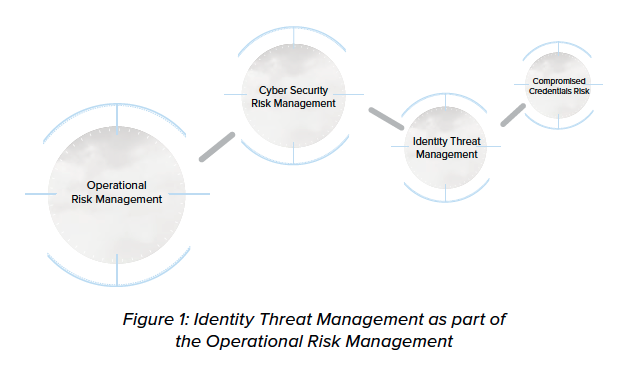
Within the cybersecurity risk itself, there are many different risks. In this paper, we will focus on Identity Threat Management and the risk of compromised credentials, which try to answer two key questions: “How at risk are my users” and “How at risk is my organization to the risk of compromised credentials.”
CYBERSECURITY RISK & IDENTITY THREAT MANAGEMENT
Because technology now has a broad and pervasive impact on the successful operation of the business, comprehensive and accurate assessment and mitigation of cybersecurity risk is absolutely essential and covers many areas of technology.
Perhaps no area of cybersecurity risk is more significant than that of Identity Threat Management as businesses ultimately harness the work of individuals who assume electronic identities within the technology infrastructure to drive the business forward. Threats to identities within the enterprise, therefore, are ever-evolving as identities provide access to business information in the form of access to critical applications and their associated data.
Threats to identities and unintended access have been leveled at enterprises as long as identities have existed in the form of password grabbers, phishing, malware, impersonation, identity fraud, social engineering, and the like. Password management, privileged access management, identity governance, and identity and lifecycle management have all been accepted ways of mitigating the many varied threats to identities, access, and data.
Past known threats, however, are not finite threats to identities, access, and data. Recently, a new and pernicious threat to identities has emerged in the form of compromising the credentials of those identities. Addressing all threats to identities, including compromised credentials that pose an enormous risk to organizations, represents a class of threat management within cybersecurity risk identified here as Identity Threat Management.
COMPROMISED CREDENTIALS RISK MANAGEMENT
Compromised credentials are an exact match of your employees’ or customers’ user IDs and passwords and are available to anyone on the outside via the Dark Web1. Because compromised credentials represent exact match credentials, are easily obtainable from the outside, and difficult to detect, they represent a very serious and pernicious threat to organizations.
The risk associated with compromised credentials lies not only in the threat of easy-to-obtain, unauthorized entry into organizations from the outside. The risk is magnified because compromised credentials actually upend many of the traditional risk mitigations organizations typically use and rely upon to bring assurance.
THREAT TO TRADITIONAL PASSWORD MANAGEMENT
The first threat to consider is toward traditional password management. Most organizations have and enforce policies around password complexity as well as frequency and causation of resets. Compromised credentials sidestep these policies since the exact match means password complexity does not matter. An exact match on a complex password is still an exact match.
The frequency of password resets2 is also affected in that forcing password resets can actually accelerate the use of reused credentials in organizations and can reset the risk profile to a higher level. This potentially elevates the cybersecurity risk through in-house processes aimed at eliminating operational inefficiencies via traditional services such as self-service password resets.
THREAT TO IDENTITY VERIFICATION SERVICES AND MULTI-FACTOR AUTHENTICATION
Exact match also makes compromised credentials a serious threat to identity verification services as well as multi-factor authentication (MFA). Many organizations continue to take pedestrian approaches to identity verification and password reset (such as through secondary email validation) and MFA. Often organizations perceive these mechanisms as “silver bullet” mitigations of threats to identities and universally accept these approaches to authentication (AuthN)3 and authorization (AuthZ)4 mechanisms as sufficient assurance.
When an attacker has a valid set of compromised credentials in hand, those credentials can often be leveraged to easily defeat commonly accepted identity verification mechanisms and circumvent MFA through disablement, interception or social engineering.
SCORING COMPROMISED CREDENTIALS RISK
To ascertain and score compromised credential risk, the following approach is intended to provide risk officers within an organization with a way to accurately measure risk and to subsequentially formulate a defense strategy through commonly accepted cybersecurity frameworks as part of its cybersecurity risk management.
The metrics used to score compromised credentials risk is as follows: Percentage of Compromised Credentials, taking into account types of credentials, Availability of Compromised Credentials as not all credentials on the Dark Web are available at once, and Percentage Convertible to Plaintext Credentials as both the ability to readily convert an organization’s passwords to plaintext as well as the additional intelligence plaintext provides increases the likelihood of a successful attack.
PERCENTAGE OF COMPROMISED CREDENTIALS
Every organization at any given time has a finite pool of credentials. The Dark Web has a large and growing pool of compromised credentials. There is a likelihood of some of those user IDs and passwords to be an exact match with credentials at your organization. How many matches (leaked credentials) your organization has divided by your total pool of credentials is “a” percentage.
Privileged credentials, even if only one or a few, pose enormous risks to organizations. To quantify this risk assessment, we are estimating the risk of privileged credentials as ten times the risk of a non-privileged, normal user credential. Each organization should determine what that number is based on the breath of privileges of its privileged user accounts and the level of damage an attacker, possessing such credentials, can do to the organization. A similar process should be followed for determining the risk multiplier for the non-user IDs.5
Recommended is a weight of ten (10) for privileged credentials, five (5) for non-user ID and power user credentials, and one (1) for non-privileged credentials. The resulting equation for determining the percentage of risk with weight is then as follows:
| (1N+5N+10N)
T |
= | Aggregate % |
Where N is the total number of compromised credentials per type (weight) divided by T, the total number of credentials an organization has. Then the aggregate percentage becomes the overall percentage of compromised credentials and is risk scored linearly.

Bear in mind, any compromised credential poses a significant threat to the organization since any access represents at least a beachhead into an organization’s technology infrastructure. This is one reason why non-user IDs, which typically exist in an unmonitored and unaccounted-for state, pose more risk than a non-privileged, normal user credential.
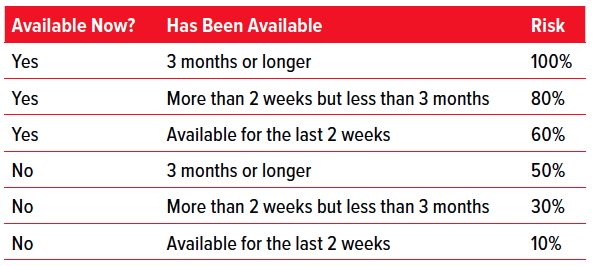
AVAILABILITY OF COMPROMISED CREDENTIALS
Not all leaked credentials are available on the Dark Web all the time. The Dark Web is like a food bazaar on a busy street in Bangkok — all kinds of credentials are offered and then suddenly made unavailable for various reasons.
Some buyers want exclusive access to types of credentials based on perceived value. For instance, credentials of a certain class or type, such as leaked credentials from a financial institution, will more likely be perceived as a high value since individuals will often create credentials of a certain kind and then reuse those same credentials across all their financial accounts, but not with their social media accounts.6
Availability is based on two factors: firstly, if a compromised credential has been available and secondly, how long it’s been available. If a compromised credential is no longer available but experienced “some” availability, then the risk is lower. If a compromised credential is currently available and has been for some time, then the risk is higher.
As data breaches with compromised credentials are the most prevalent attack vector7, the risk around availability is relatively linear and deterministic with the overall risk score for an organization based on the aggregate risk of any and all compromised credentials found through a trusted compromised credentials intelligence source.
PERCENTAGE CONVERTIBLE INTO PLAIN TEXT
Finally, the percentage of passwords an organization has that are easily convertible to plain text is an important indicator of risk.
When passwords are presented to a trusted compromised credentials intelligence source such as VeriClouds as seed data to analyze and find compromised credentials, those passwords are typically checked by the service to see how easily they can be converted to plain text.8 Any success greater than 20% is considered a high risk to an organization. In this case, length and complexity do actually matter.
The risk around percentage convertible into plain text is also relatively linear and deterministic and can be provided based on an overall aggregate score through the use of a trusted compromised credentials intelligence source.

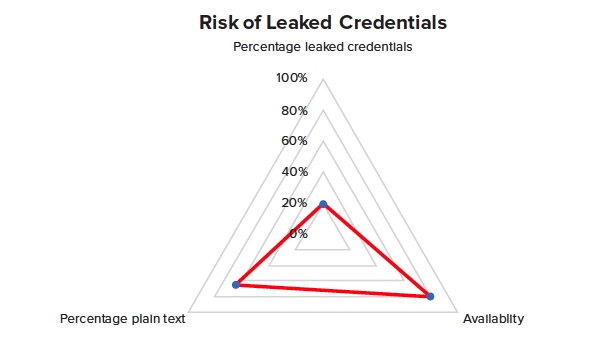
RISK SURFACE
Once all risk scoring for compromised percentage, availability, and plaintext percentage is known, then the scores can be triangulated according to the three points in a spider chart to visualize the total risk surface. The greater the risk surface, the greater the aggregate risk to an organization.
A sample is provided here for visualization.
DOWNLOAD SCORING GUIDELINES
In an effort to jumpstart your organization in assessing your actual cybersecurity risk in the area of Identity Threat Management for compromised credentials, visit this link, or click on the page thumbnail below to download a concise PDF formatted version of the scoring approach described.

Of course, again, the use of these scoring guidelines requires access to intelligence through a trusted compromised credentials intelligence source to determine whether or not your organization has compromised credentials, which ones are compromised and totals. But once this intelligence is obtained, the risk can be readily identified through the process outlined herein.
FRAMEWORK FOR COMPROMISED CREDENTIALS LINES OF DEFENSE
Once an organization has workable metrics around scoring the cybersecurity risk of compromised credentials, it can plug those metrics into many of the well-known cybersecurity frameworks available for assessing and mitigating that risk through lines of defense and use of tactical measures. A Basel Framework is discussed here as an example.
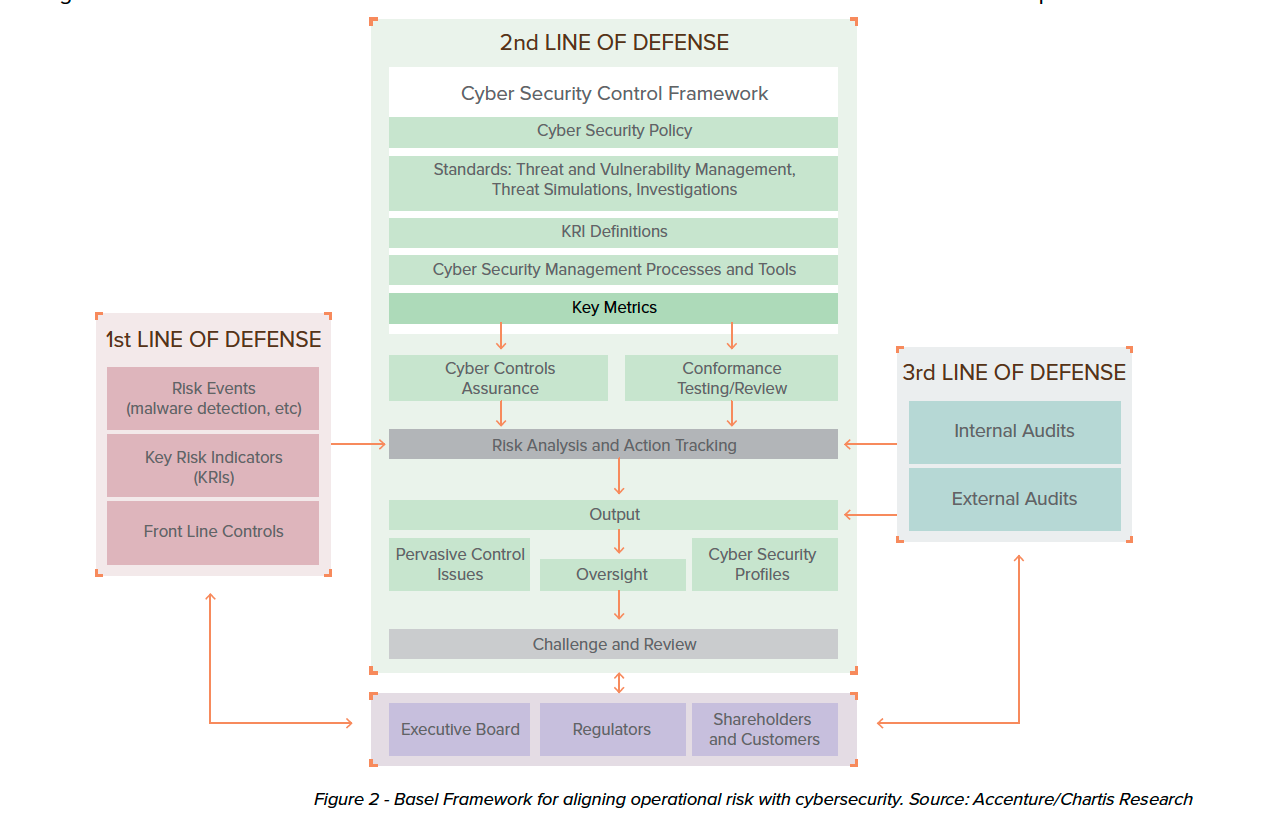
First Line of Defense: Risk Events, Risk Indicators & Front Line Controls
Risk Events for compromised credentials are simply the positive occurrences of compromised credentials to an organization. This indicates compromised credentials exist.
The Risk Indicators are the scoring metrics already laid forth in Scoring Compromised Credentials Risk.
Front Line Controls for compromised credentials is the use of a trusted compromised credentials intelligence service that allows the tactical implementation of both active and passive technical use cases within IAM to provide real-time and batch implementation for compromised credentials mitigation.
Second Line of Defense: Cybersecurity Policy, Management & Key Metrics
Cybersecurity Policy for an organization needs to define the risk from compromised credentials, stipulate that compromised credentials will not be allowed, and how compromised credentials will be mitigated and disallowed at the tactical level through defined technical use cases.
Management of compromised credentials needs to take place at the tactical level that exists through the implementation of technical use cases stipulated in the Cybersecurity Policy.
Key Metrics used to measure and report the effectiveness of both the policy and management of compromised credentials are the metrics again defined in Scoring Compromised Credentials Risk. Over time, the risk surface within an organization through policy and management should show a greatly reduced attack surface.
Third Line of Defense: Internal Audit
Internal Audit is an implemented process that checks on a regular basis to ensure the policies, management, and mitigating controls for compromised credentials have been implemented, remain implemented, and that appropriate actions stipulated in the policy have been taken.
ASSESSING THE RISK OF COMPROMISED CREDENTIALS
Compromised credentials are a rapidly emerging and dangerous risk to organizations that require senior cybersecurity and risk officers within to take notice, assess, and sufficiently address. It is hoped this paper helps highlight, articulate, and provide proper guidance in scoring, assessing, and building lines of defense through accepted cybersecurity frameworks to mitigate this risk.
1 Dark Web – used as an aggregate term for dark web, deep web and surface web
2 Not withstanding the fact NIST has already determined past policies around traditional password reset policies not only does not lower risk, but in fact likely increases it.
See new NIST 800-63-3 Guidelines.
3 Authentication (AuthN): Determining identity – is a business entity who or what it claims to be?
4 Authorization (AuthZ): Determining a given identity’s access – does or should an authenticated identity have access to a technology asset?
5 IDs created for non-user accounts such as application IDs, testing IDs, FTP IDs, layered product IDs, etc.
6 There exists a very real sense in which credentials get “risk scored” and categorized at the moment of password creation by the users themselves. This greatly aids the underworld in terms of first level analytics around value, vector and probability.
7 81% of reported data breaches are the result of weak or stolen credentials, 2017 Verizon Databreach Investigations Report
8 Success of converting passwords to plain text depends on the hash used, whether they are salted and the length and complexity of the password.
