Automated Credential Security
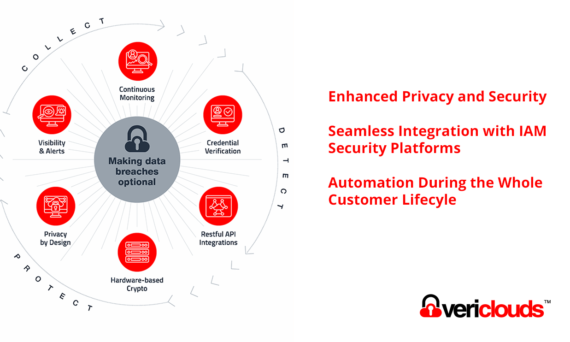
Automate identity threat intelligence, satisfy regulatory compliance requirementsWhat we do VeriClouds Integrates with Enterprise Security | VeriClouds Actively Stops Automated Account Takeovers Before They Start | VeriClouds Enhances Privacy, Aligning with NIST 800-63b Seamless Integration Instant Insights Automated Remediation VeriClouds’ CredVerify offers a SaaS platform delivering real-time, comprehensive threat detection and mitigation in a native cloud-based solution, simplifying […]